Microsoft typically releases updates for Windows as part of its monthly “Patch Tuesday” blitz, but the company took the unusual step of releasing an emergency out-of-band security update late Monday night to fix the critical “PrintNightmare” vulnerability published (and deleted) by researchers last week—even for Windows 7. Bottom line? Update your Windows PC pronto… but the patch not fix all PCs if you’re connected to a local network.
PrintNightmare attacks the Windows Print Spooler service, which runs by default. “A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations,” Microsoft’s executive summary states. “An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
In other words, PrintNightmare lets attackers into your system over the internet, and then they essentially have free rein over your computer. “All supported editions of Windows are affected,” Microsoft warns.
Microsoft released emergency security patches for most versions of Windows 10, Windows 8.1, Windows RT 8.1, and various Windows Server installations. “Supported versions of Windows that do not have security updates available on July 6 will be updated shortly after July 6,” Microsoft says. Driving home how severe this vulnerability is, the company even released a PrintNightmare security fix for Windows 7, an operating system that was forced into retirement last year.
 Brad Chacos/IDG
Brad Chacos/IDGThe company lists these patches as a temporary fix, and security researcher Matthew Hickey says that the patch only nullifies the danger of remote execution. That means that if an attacker manages to physically get ahold of your PC, they could still leverage PrintNightmare to take control of it. (Update: After the patch was released, security researchers discovered that fully patched systems could still be attacked remotely if your administrator enables certain settings to enable a network printer feature called Point and Print, Ars Technica reports.) But for the vast majority of people, simply using personal computers in their home, shutting down the ability for this vulnerability to work over the internet should effectively render it obsolete.
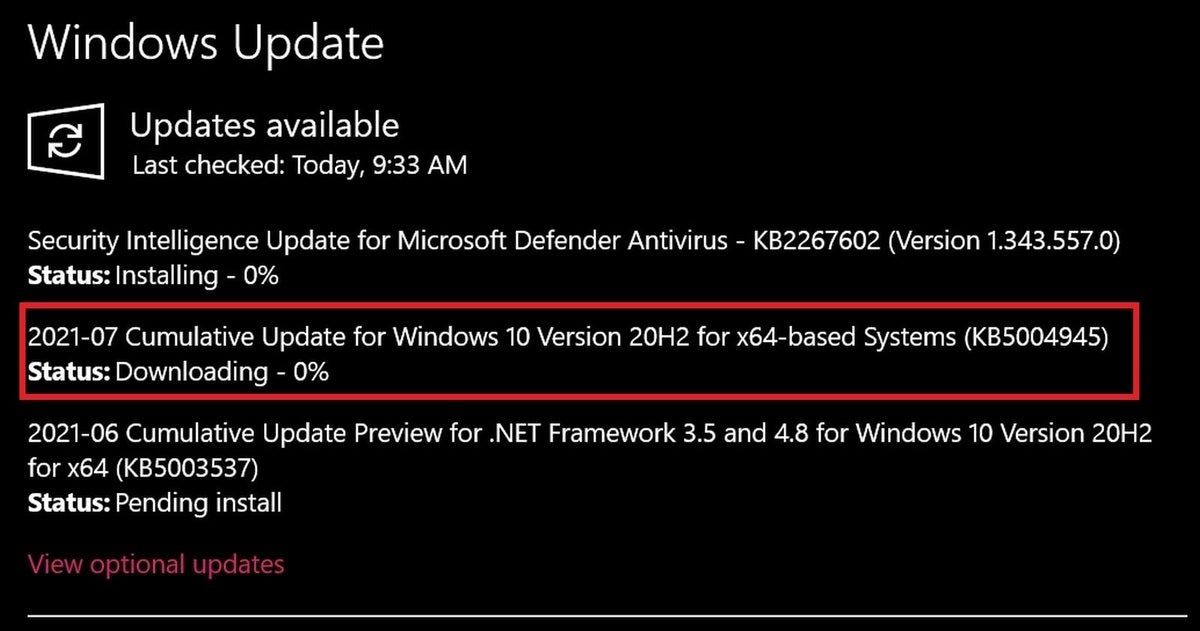
So get to downloading, folks. Checking Windows Update on my PC showed the PrintNightmare patch (KB5004945 for my version of Windows 10) already available. While you’re being safety-minded, make sure to install an antivirus and perform the five easy tasks that supercharge your security if you haven’t already.
Editor’s note: This article originally published on July 7, but was updated July 8 to mention that Point and Print could still leave fully patched PCs vulnerable to remote execution.